As you may have already heard, the worst bug in OpenSSL history went public yesterday, dubbed Heartbleed. While we can go deeper into the technical details of it later, the short version is that OpenSSL, the library used to encrypt much of the web running on Linux and Apache has been vulnerable for up to two years.
The vulnerability reveals the contents of memory on any server running an unpatched version of OpenSSL, 64KB at a time. This effectively means that with enough polling, one could reconstruct the private keys to SSL certificates used on affected servers, plain-text passwords, emails, usernames, and anything else that might be floating around in memory on an affected server.
While a few big sites and service providers received early notice of the bug and were able to patch their systems before news went public, the rest of the web running OpenSSL has been scrambling to patch their systems (which requires a reboot... for those of you who need to patch your own systems to 1.0.1g).
While we can't say for sure if the private SSL keys of affected sites have been compromised, as the bug has been in the wild for 2 years, we have to assume they are. As such, many sites are issuing new private keys for their SSL certificates, and revoking the old ones to make sure any compromised keys can't be used going forward.
So What Does All This Have to Do with Chrome?
When an SSL certificate is revoked, your browser won't trust it—but that only works if your browser knows that the certificate has been revoked. Chrome's default settings do not automatically check to see if certificates have been revoked. As such, a compromised SSL certificate could be set up on a spoofed website, and Chrome would show the green lock indicating it's secured.
How to Fix Your Chrome Settings
Simply enable the check for server certificate revocation. To do this:
- Click the Chrome "menu" button in the upper right.
- Click Settings.
- Scroll down and click "Show advanced settings...".
- Scroll down to the HTTP/SSL headline and check the box labeled "Check for server certificate revocation".
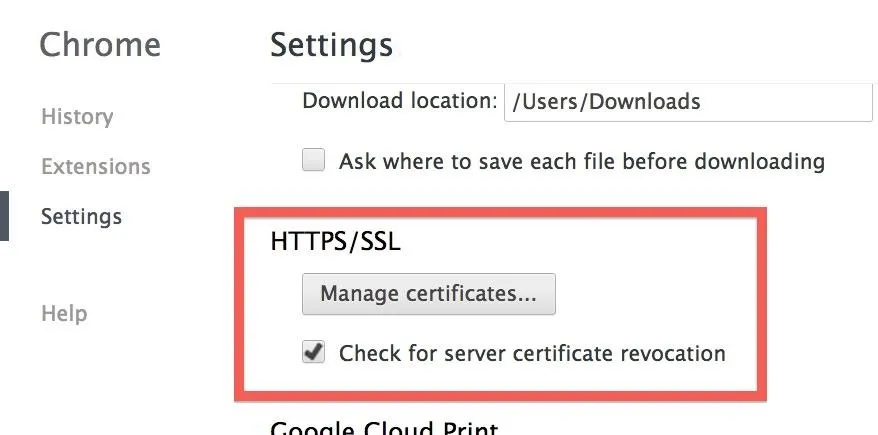
That's it. You can now browse the web knowing that any revoked certificates will no longer be trusted.
But What About All the Unpatched Websites?
There are still many encrypted sites out there that are unpatched as of yet. To make sure your login credentials don't end up floating around in memory, ready to be picked off, refrain from logging into any HTTPS websites until they've patched their servers.
You can check to see if a domain is vulnerable using this website set up by Filippo Valsorda.
It will show red if vulnerable. If you get a timeout, or it shows green, then you can rest easy knowing the server is not using one of the vulnerable versions of OpenSSL, and is safe to log in to.




Comments
No Comments Exist
Be the first, drop a comment!